Issue
TGML Graphic worked without error in EcoStruxure Building Operation 2.0 WebStation. After an upgrade to 3.0, WebStation displays one of the following errors on page load:
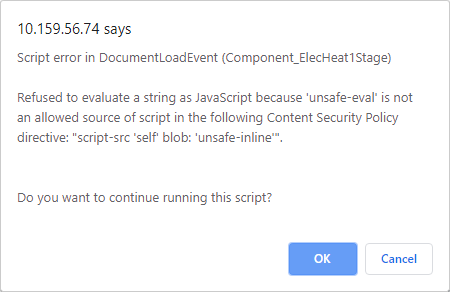
Script error in DocumentLoadEvent (Component_Name)
Refused to evaluate a string as JavaScript because 'unsafe-eval' is not an allowed source of script in the following Content Security Policy directive: "script-src 'self' blob: 'unsafe-inline'".
Do you want to continue running this script?
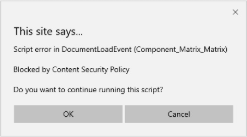
This site says...
Script error in DocumentLoadEvent (Component_Name)
Blocked by Content Security Policy
Do you want to continue running this script?
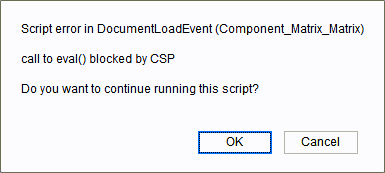
Script error in DocumentLoadEvent (Component_Name)
call to eval() blocked by CSP
Do you want to continue running this script?
Product Line
EcoStruxure Building Operation
Environment
- Building Operation 3.0
- TGML Graphics
Cause
A new security setting in 3.0 disallows eval() statements by default in TGML JavaScripts presented in WebStation. An eval() statement executes a string of characters as code, which can open security vulnerabilities if enabled, something akin to a SQL injection or cross-site scripting attack. If graphics were created in earlier versions and relied on eval() to execute dynamic code, the user will be notified upon opening the graphic in 3.0 WebStation.
Resolution
Any graphics relying on eval() to execute dynamic code should have their JavaScript functions rewritten to avoid use of eval(). This is the preferred approach with respect to cyber-security.
Work-Around
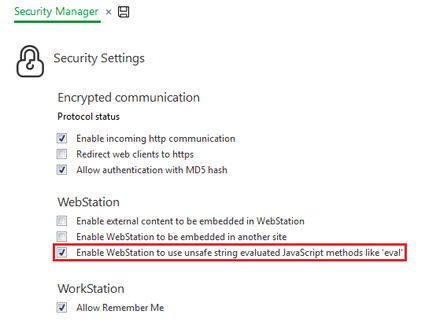
It is possible, but not recommended, to disable the new security check in WebStation TGML graphics.
- Within WorkStation open the Control Panel
- Go to Security Settings
- Check the box for "Enable WebStation to use unsafe string evaluated JavaScript methods like 'eval'
For more information, see Web Help article: Enabling WebStation to Use Unsafe JavaScript Methods.
For the latest solution to this issue please refer to: Cannot Open Graphics in WebStation