Industrial Cybersecurity Roadmap for Final Users
Industry 4.0 Blog
This blog is addressing the Industry 4.0 and includes news and information aroud topics as smart manufacturing, artificial intelligence and Industrial Internet of Things (IIoT).
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Email to a Friend
- Printer Friendly Page
- Report Inappropriate Content
Link copied. Please paste this link to share this article on your social media post.
Industrial Cybersecurity Roadmap for Final Users
Originally published on Industry 4.0 Blog by mateomadariaga | November 04, 2020 11:07 AM
The Industrial Scenario
Cybersecurity’s importance is being driven by the global business environment becoming increasingly interconnected and reliant on data and digital technologies. As a result, organizations need to think of cybersecurity not just in terms of compliance and risk mitigation, but as an essential business function that is fully embedded in processes and systems.
Companies in the industrial sector are most exposed to the changes that digitalization is producing. These changes have arisen from the progress that has taken place in today’s industrial ecosystem; industrial control systems (ICS) optimization, new internet of things (IoT) solutions, Cloud Computing, Big Data and Artificial Intelligence platforms among others. Digital transformation brings several benefits such as boosting the performance of industrial assets, enhances efficiency and productivity, accelerates reaction to changes in trends/demand, fosters competitive advantage, allows predictive and remote maintenance, and most importantly, it optimizes costs and operational expenditures.
However, new technology innovations also bring newfound risks. As we connect our factories, machinery, and operational technology (OT) systems to the internet we are also exposing them to new potential threats. This is a well known saying in the cyber world: if connected you are being hacked. We need to assume cybersecurity as a prerequisite for all digital transformation projects and this implies to deal with new problems in both greenfield and brownfield scenarios.
Cybersecurity Roadmap
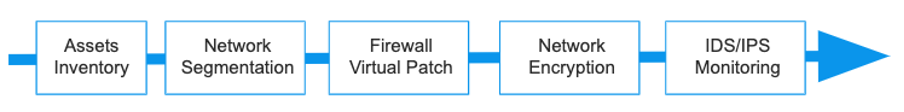
Once the customer is committed to improving his security level, he needs to build a cybersecurity plan to analyze his current situation and evaluate the gaps. This is an essential tool for any organization that seeks to protect its customers, employees and corporate information. The first step in the cybersecurity roadmap is to understand where a company is at present, and where you would like to be in the future. Characteristics and functions of the cybersecurity approach have to be defined, including risk compliance, security administration, security architecture and design, and security operations.
- Asset inventory management
At this point, the customer needs to understand the size of the problem and make some research on how his infrastructure looks. At this point, the customer needs to upgrade the last documented version of the architecture and check how the current network diagram differs from it by means of an asset inventory. Sometimes, legacy infrastructures that have been built several years ago have no previous documented version or have not implemented an automatic asset inventory solution.
The most usual scenario is that legacy industrial plants present a flat network. This means that the field devices are all together interconnected. This paradigm was really extended before the 2000's as it was the easiest way to interconnect the network devices and also minimize the maintenance. That was a good idea in those days, because there was no malware still or potential cyberthreats.
Nevertheless, with the advent of Industry 4.0, we are interconnecting through the internet industrial infrastructures, manufacturing factories, water and wastewater systems, electric grids... The reverse side of the coin is that these networks are exposed to the internet and its threats. If one of the devices on the networks get infected, these malicious code can be spread through the plant/facility, disrupting the functioning of the automation equipment, as there is barely any network segmentation in legacy infrastructures.
- Network Segmentation
In order to overcome these problems, segmentation is highly encouraged. Segmentation divides an industrial network into smaller parts. The purpose is to improve network performance and security. There are different ways to achieve this goal depending on the constraints and customer requirements. Typically, at this point, industrial processes are segregated in functional units, controlling how traffic flows among the parts. So enterprises need to understand the risks of the overall system when designing this new network diagram, in order to isolate the most critical units and set up new rules and connections based on security requirements.
- Firewall and Virtual Patching
At the same time, one establishes secure communication conduits defining which zone or segment can talk with which other and through which network services. Thanks to that, the surface attack is reduced. Different techniques and products can be used depending on the likelihood of vector attacks in these functional units. For example, in M2M communication a stateful firewall could be enough. However, in a zone with engineering workstations, a deep-packet-inspection (DPI) firewall is mostly recommended.
- Communication and devices hardening
Most of the communication protocols in the industrial field do not implement the basic cryptographic techniques to ensure the privacy, confidentiality or integrity of the data. Without this protection, one can manipulate the information sent through the network or impersonate an engineering workstation. As a result, data can be poisoned or misused in analytics or decision-making processes, which can lead to interrupt the operation of the plant, huge economic losses, devastation environmental problems or even could cost lives in critical scenarios.
The only way to increase the security in this case is to implement advanced cryptographic techniques, in those protocols or in the communication or in the network system. Unfortunately, this step is quite difficult as most of the time in legacy infrastructures you cannot modify the architecture or the protocols used. Properly setting encryption in key communications or hardening risky channels mitigate most of the potential risks.
- IDS/IPS Monitoring
Once the security level of the network meets the requirements of the risk manager, the challenge is to keep it against new threats or attack vectors. Monitorization plays a key role in this phase. Different tools and techniques can be used to ensure visibility and persistent threat detection.
Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) detect potential malicious activities or security policies violations. Usually IDS/IPS creates a base-line and when an anomaly is detected, it sends an alarm to Security Information and Event Management (SIEM). This alarm is managed by the qualified personnel and the proper actions are done according to the criticality of the alarm. If the event is not discarded, the Incident Response team will be involved to solve any problem and recover the normal functioning of the system. Finally, note that these solutions do not prevent attacks but help to detect persistent threats.
Summary
The cybersecurity roadmap will slightly change per segment and end-user, according to its requirements, needs and circumstances. This roadmap provides a defense-in-depth approach and can be enriched by zero-trust point of view. Building a cybersecurity roadmap doesn’t have to be laborious or overly theoretical. By beginning with high-level objectives and adding details as you progress and mature, you’ll be well on your way to success.
Trust Enigmedia as your cybersecurity partner, our objective is to embrace digital transformation in critical infrastructures and the industrial sector. We provide easy-to-deploy and cost-effective native cybersecurity solutions to protect industrial networks, guiding our partners along the cybersecurity roadmap, ensuring optimum protection at all stages. Mercury Cipher is our native OT cybersecurity solution, allowing secure data collection, communications protection, network segmentation, firewalling, remote access, and intrusion detection, becoming a perfect tool for industrial environments. For more information about our unified threat manager (UTM) solution, visit our Mercury Cipher product page on Schneider Electric Exchange Shop.
- Tags:
- asset inventory management
- control systems optimization
- cybersecurity roadmap
- Digital transformation
- english
- industrial cybersecurity
- IoT solutions
Author
Link copied. Please paste this link to share this article on your social media post.
Would you like to add a comment?
All registered members have full access to the Community and can post comments and start topics.
Create your free account or log in to subscribe to the forum - and gain access to more than 10,000+ support articles along with insights from experts and peers.